Data Mining Classification Approaches for Malicious Executable File Detection - Document - Gale Academic OneFile
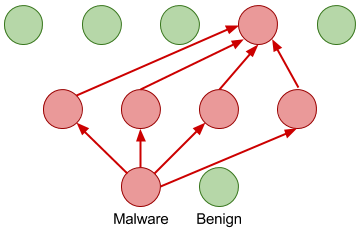
![PDF] Malicious Executables Detection Algorithm Research Based on Immune System Principles by Guo Zhen-he · 2374331249 · OA.mg PDF] Malicious Executables Detection Algorithm Research Based on Immune System Principles by Guo Zhen-he · 2374331249 · OA.mg](https://og.oa.mg/Malicious%20Executables%20Detection%20Algorithm%20Research%20Based%20on%20Immune%20System%20Principles.png?author=%20Guo%20Zhen-he)
PDF] Malicious Executables Detection Algorithm Research Based on Immune System Principles by Guo Zhen-he · 2374331249 · OA.mg
A state-of-the-art survey of malware detection approaches using data mining techniques | Human-centric Computing and Information Sciences | Full Text

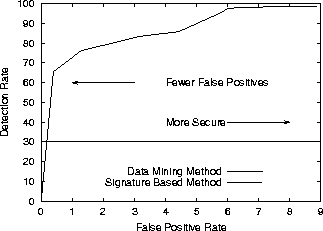
PPT – Data Mining for Security Applications: Detecting Malicious Executables PowerPoint presentation | free to view - id: 442827-MmMwZ

Improving malware detection using multi‐view ensemble learning - Bai - 2016 - Security and Communication Networks - Wiley Online Library
![PDF] A survey of data mining techniques for malware detection using file features | Semantic Scholar PDF] A survey of data mining techniques for malware detection using file features | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/9285f7d70ffc2ac0aea78e7a6ba1cb9a9f967e81/2-Table1-1.png)
PDF] A survey of data mining techniques for malware detection using file features | Semantic Scholar

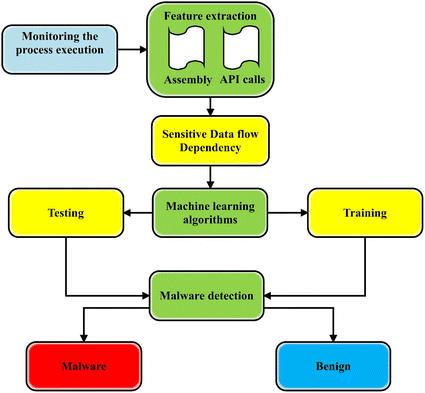
Shows the malware detection procedure of the proposed method: First... | Download Scientific Diagram

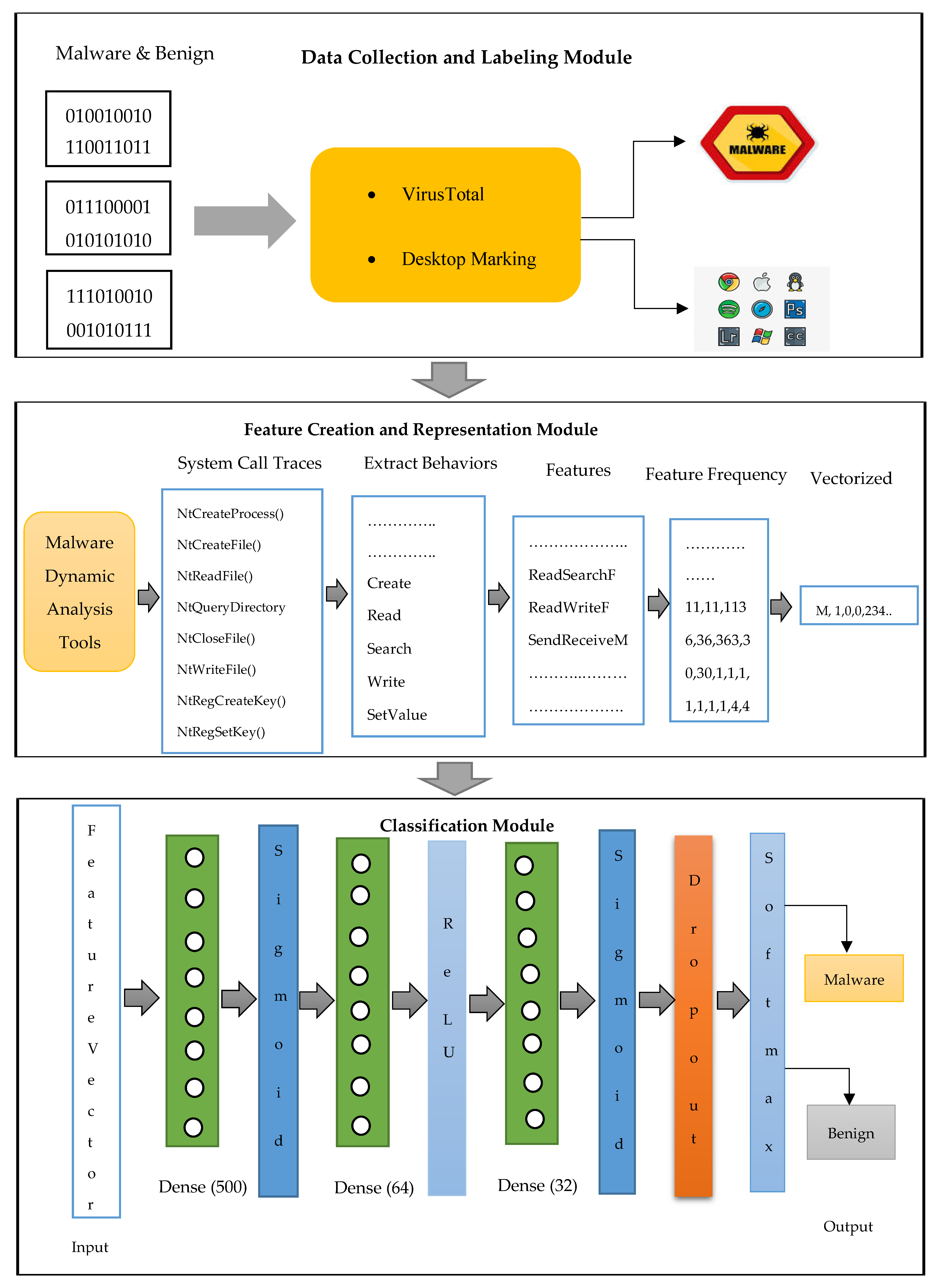
A learning model to detect maliciousness of portable executable using integrated feature set - ScienceDirect


![IJET-V1I2P2] Authors :Karishma Pandey, Madhura Naik, Junaid Qamar,Mahendra Patil IJET-V1I2P2] Authors :Karishma Pandey, Madhura Naik, Junaid Qamar,Mahendra Patil](https://cdn.slidesharecdn.com/ss_thumbnails/ijet-v1i2p2-150423020658-conversion-gate02-thumbnail.jpg?width=640&height=640&fit=bounds)
![PDF] A Static Malware Detection System Using Data Mining Methods | Semantic Scholar PDF] A Static Malware Detection System Using Data Mining Methods | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/d765915dbe7e153b1d55e843a2df2684c66220d0/3-Figure1-1.png)


![PDF] Data mining methods for detection of new malicious executables | Semantic Scholar PDF] Data mining methods for detection of new malicious executables | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/31cfc6e2281426f4dd7325d73e105dc10bf5cdd5/5-TableI-1.png)

