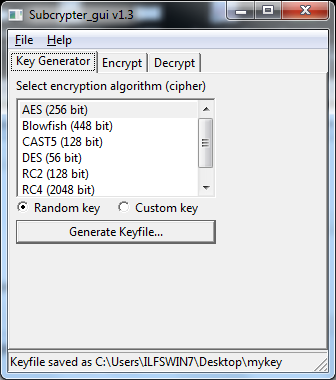
Cracking RSA — A Challenge Generator | by Prof Bill Buchanan OBE | ASecuritySite: When Bob Met Alice | Medium

CJMCU 608 Cryptographic Key Storage Random Number Generator Signature Encryption Decryption Module|encryption keys| - AliExpress

Enhanced key-generation algorithm using MRMCTT in Data encryption standard algorithm | Semantic Scholar
![PDF] Public Key Cryptosystem Technique Elliptic Curve Cryptography w ith Generator g for Image Encryption | Semantic Scholar PDF] Public Key Cryptosystem Technique Elliptic Curve Cryptography w ith Generator g for Image Encryption | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/d4cb05572af274a00ca4425ffbf51df65279c370/3-Table2-1.png)
PDF] Public Key Cryptosystem Technique Elliptic Curve Cryptography w ith Generator g for Image Encryption | Semantic Scholar

Example of an embedded encryption scheme: real time image encryption... | Download Scientific Diagram