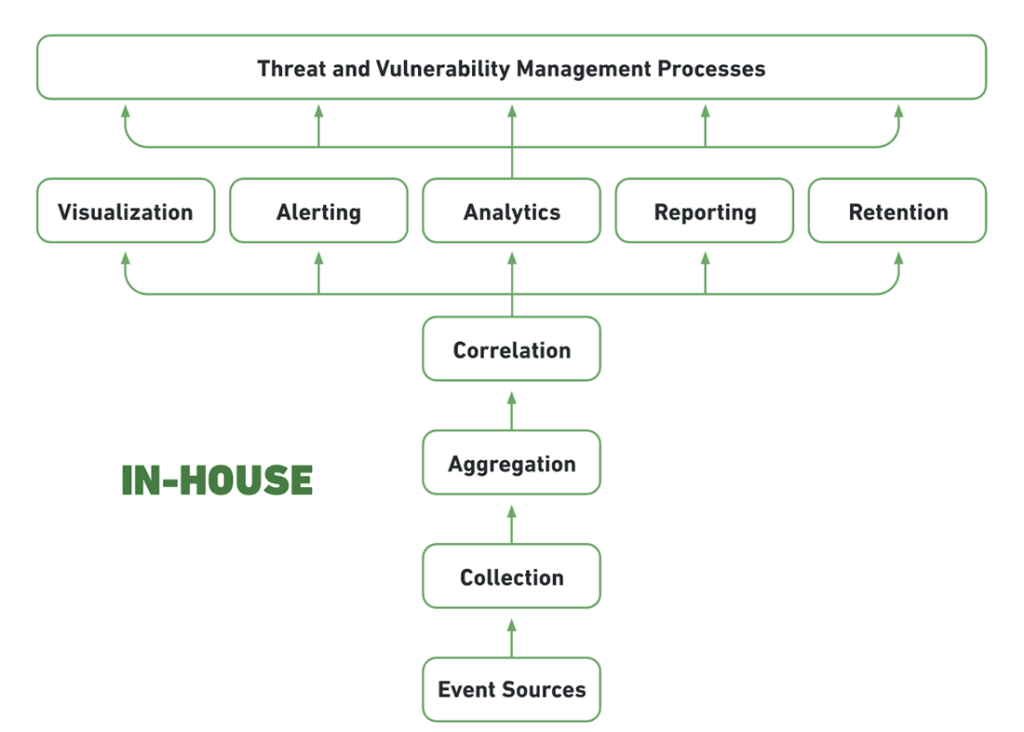
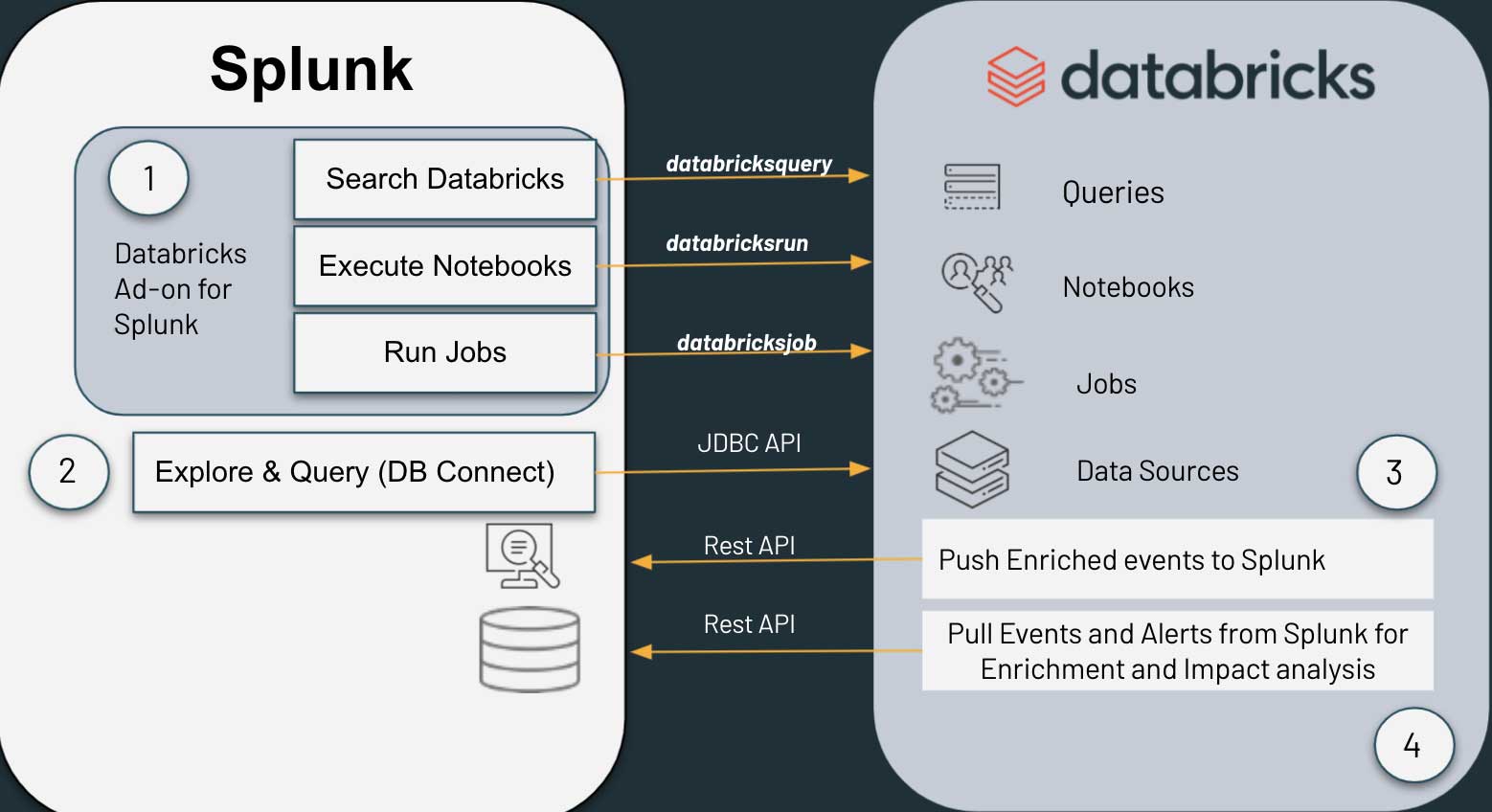
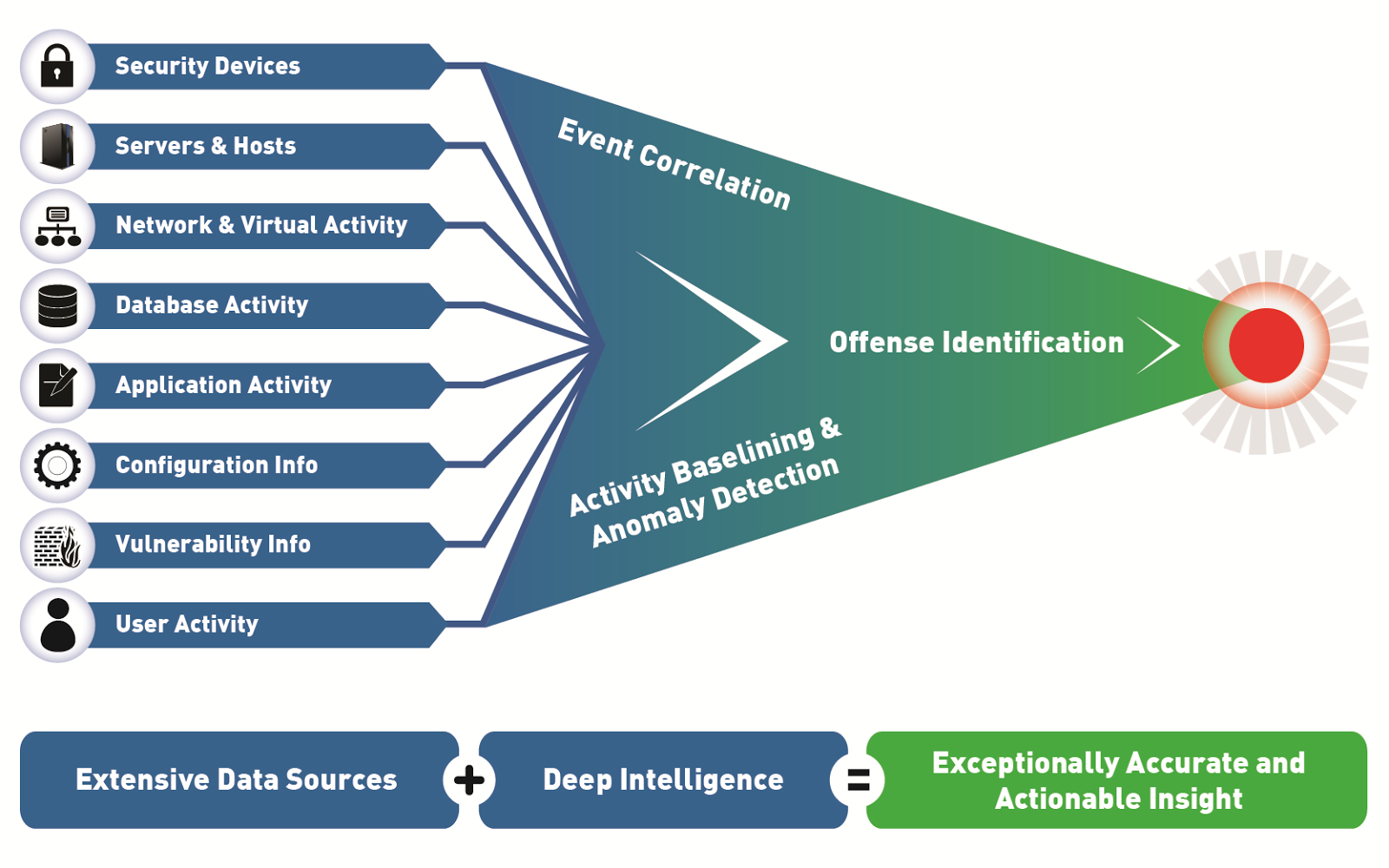
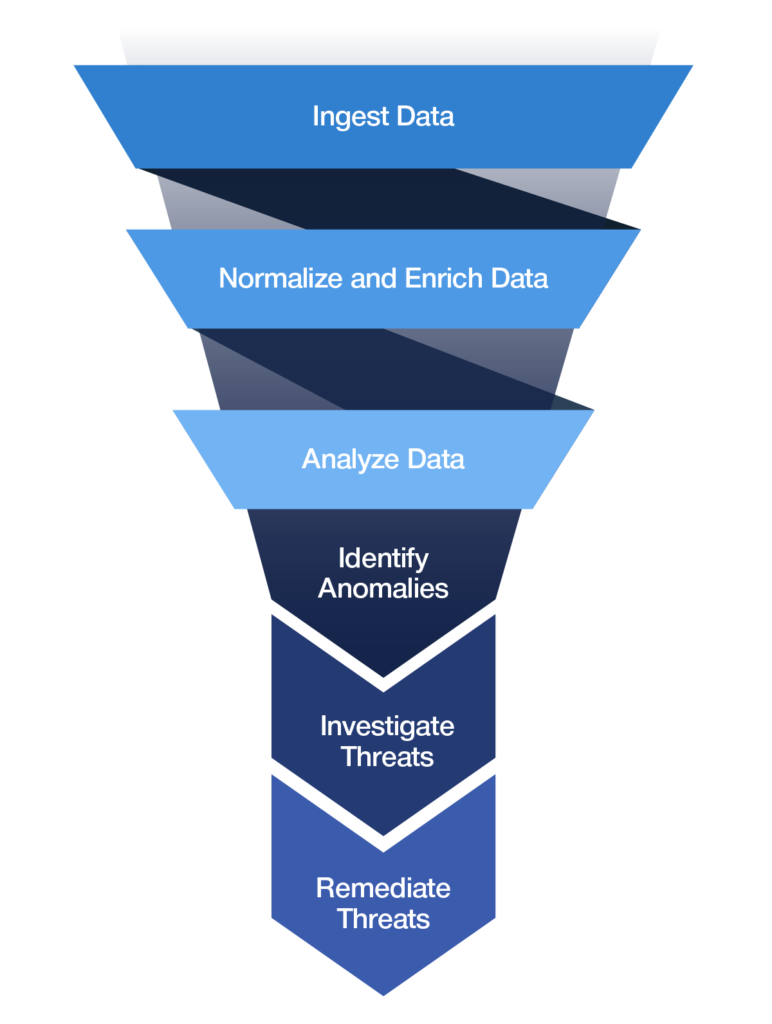
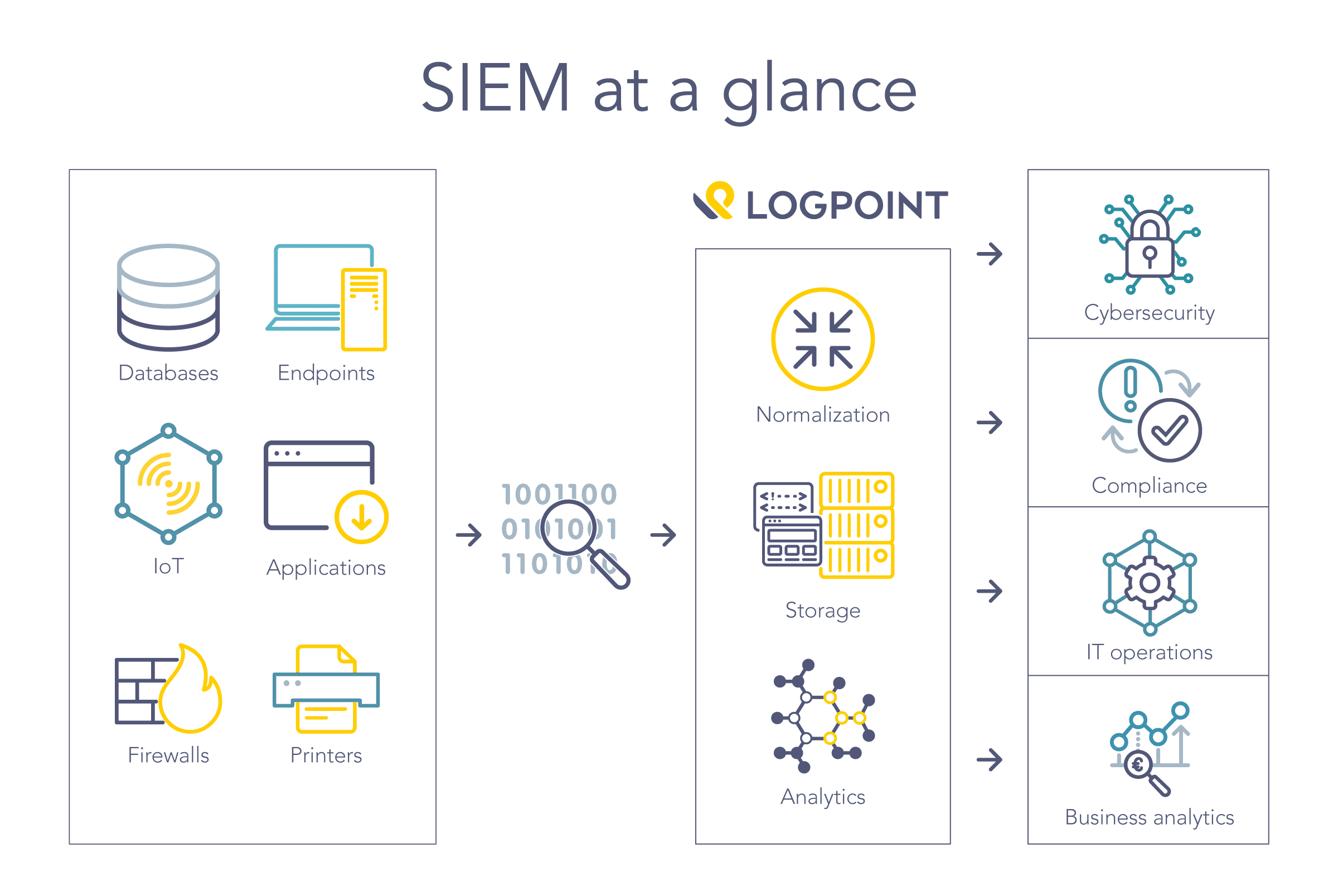
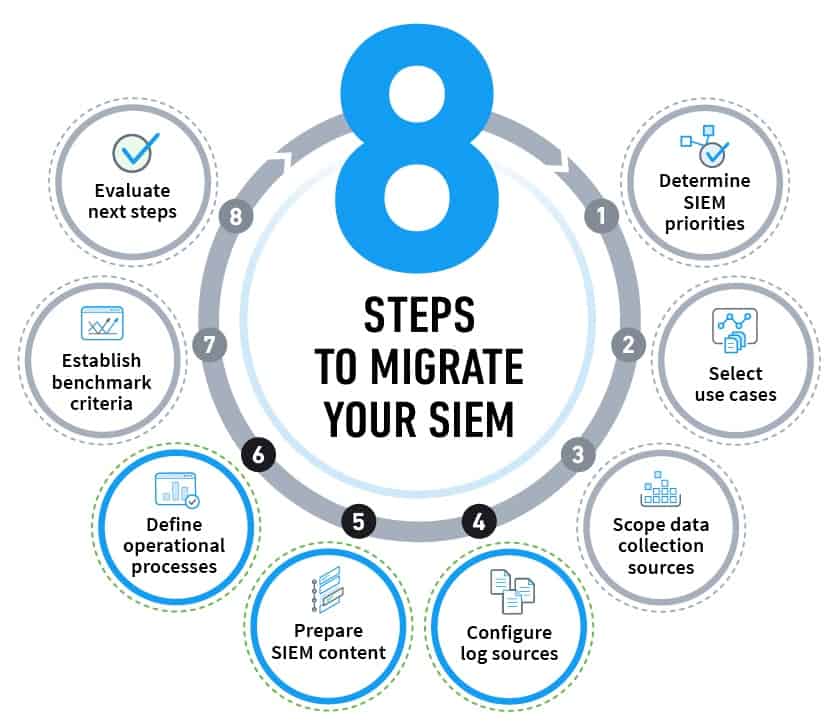
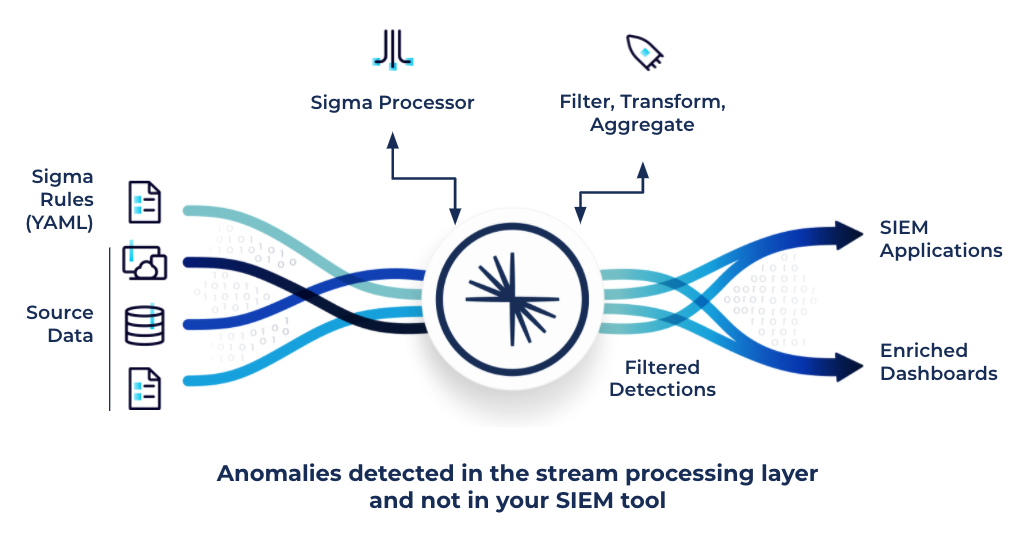
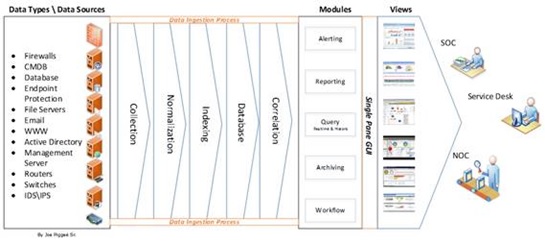
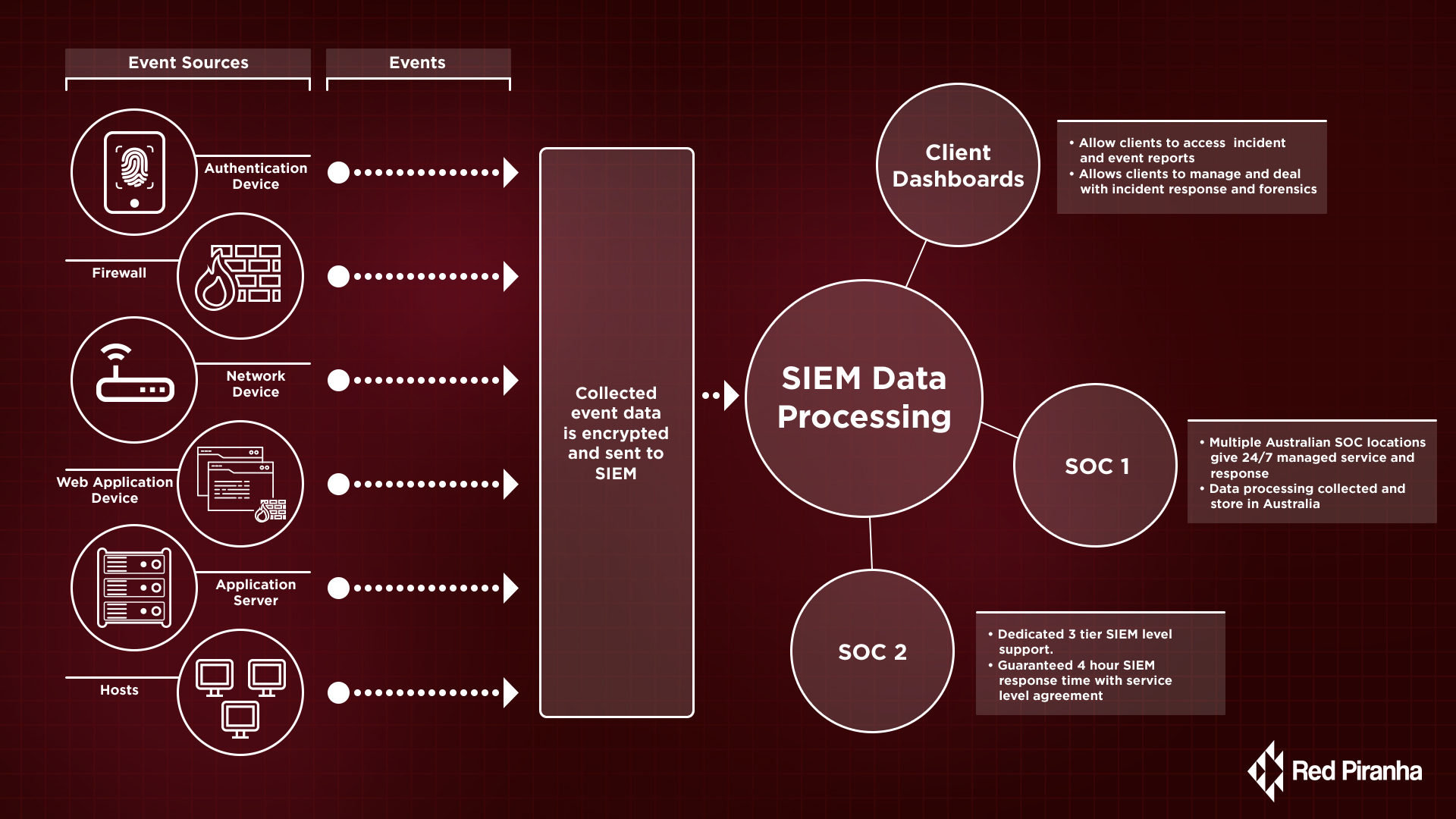
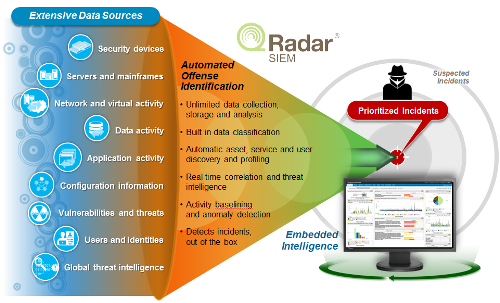
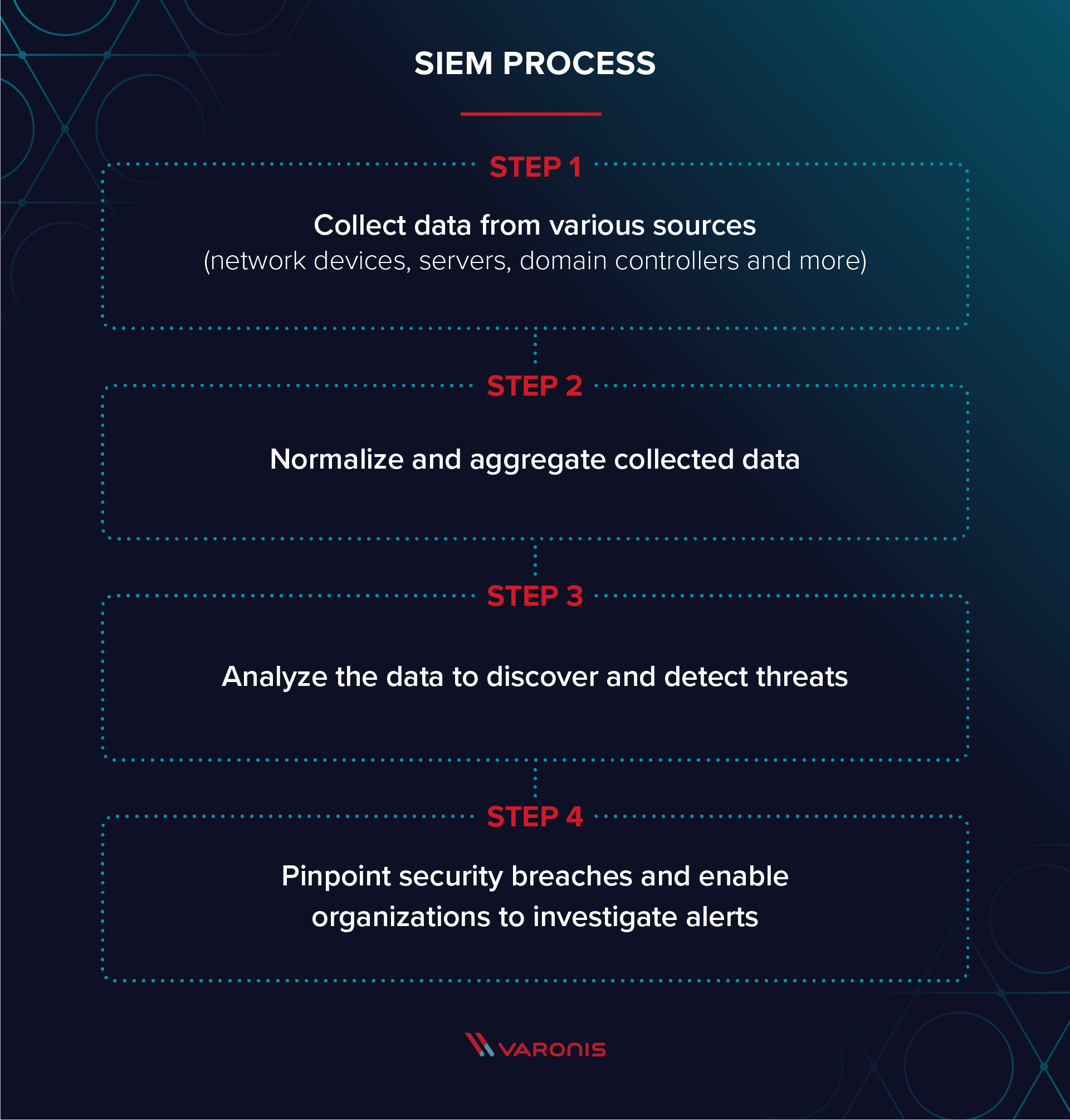
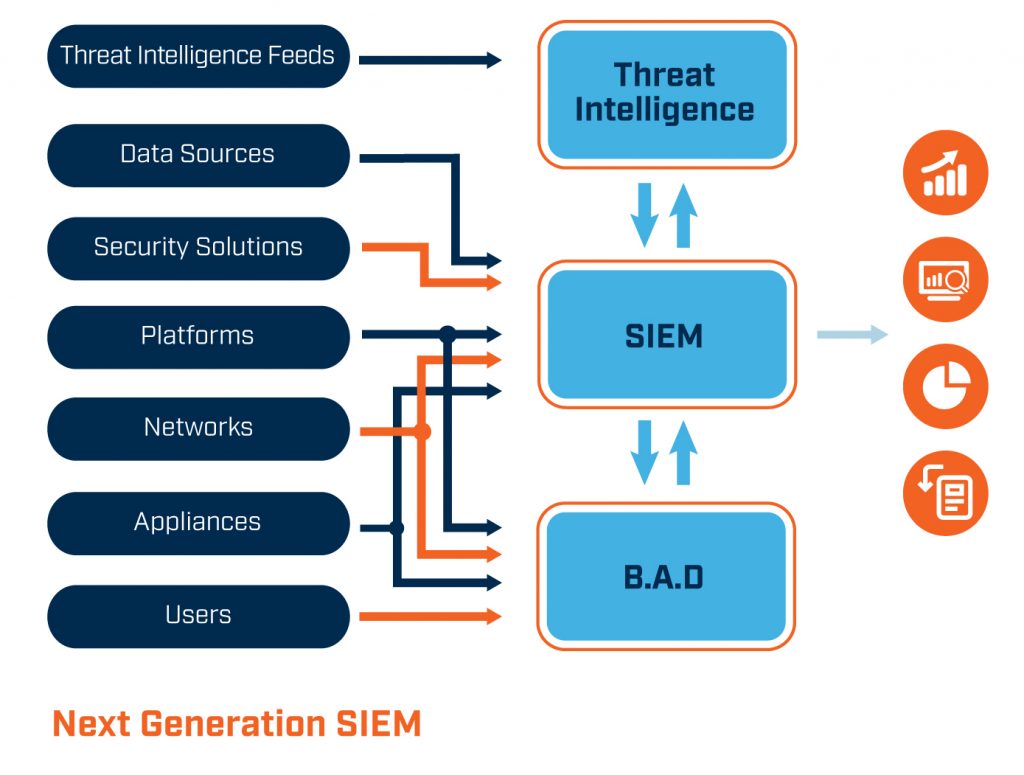
What Is Security Information and Event Management (SIEM)? Definition, Architecture, Operational Process, and Best Practices | Spiceworks It Security
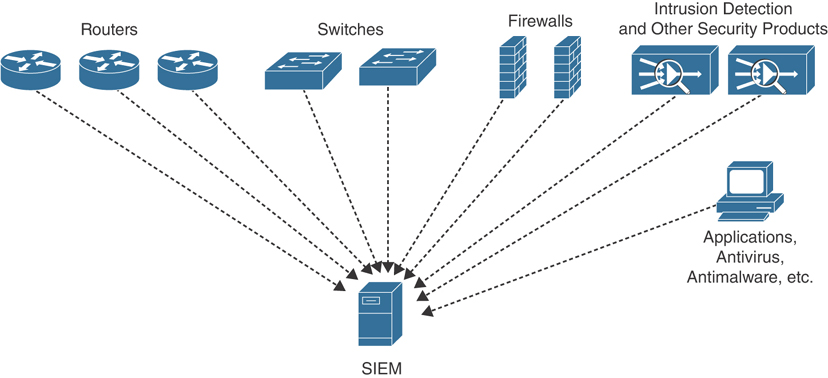
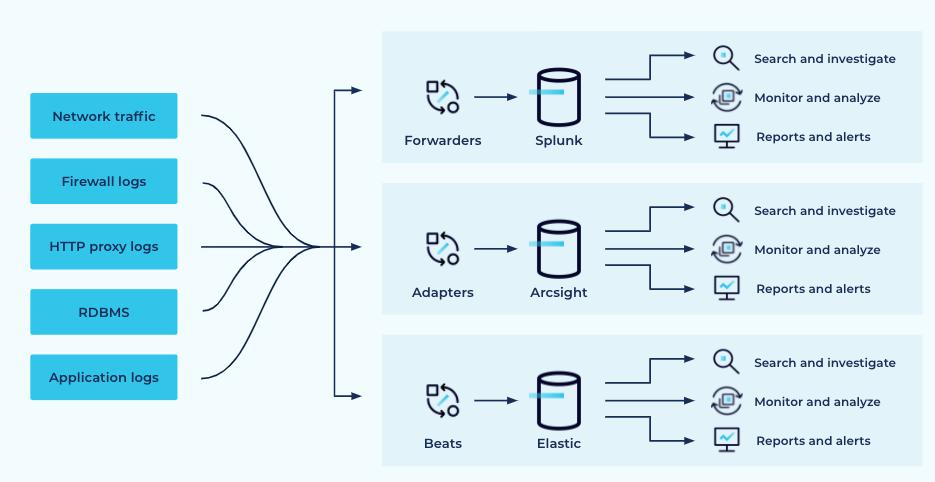
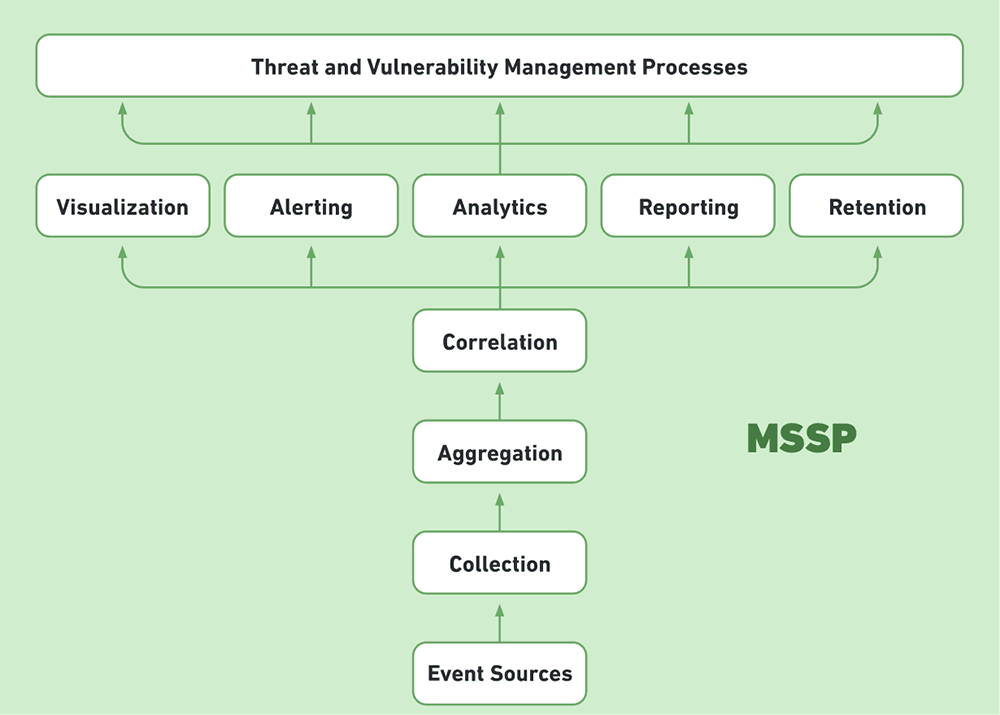
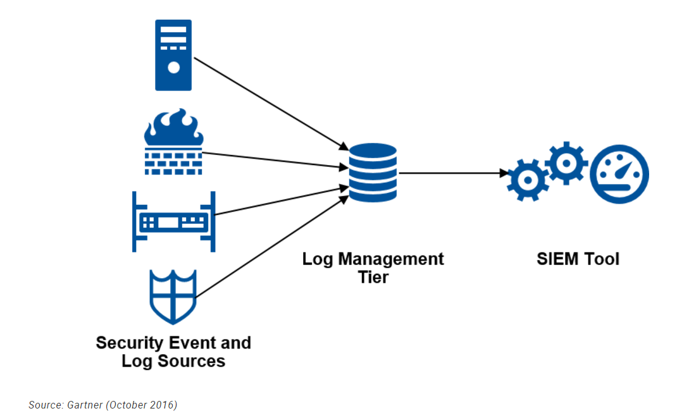
Logs and Security Information and Event Management (SIEM) | Summarizing the Techniques Used in Security Assessments | Pearson IT Certification